Part Three: Loss or Theft of Equipment or Data
By: R. Christopher Dix, Esq. and Kayla A. Haines, Esq.
Cyberattacks are a growing threat across all commercial sectors. For the healthcare industry, cyberattacks are particularly troubling because they threaten not only the security of an organization’s systems and information, but also the health and safety of patients. Every healthcare organization must face this reality. Most try to avert cyberattacks, but even the most hypervigilant healthcare organizations are vulnerable to attackers that are adapting to increased security measures, systems, and processes.
The Department of Health and Human Services published a report earlier this year entitled “Health Industry Cybersecurity Practices: Managing Threats and Protecting Patients” (the “Report”). The Department collaborated with industry partners to develop “practical, understandable, implementable, industry-led, and consensus-based voluntary cybersecurity guidelines to cost-effectively reduce cybersecurity risks for healthcare organizations of varying sizes, ranging from local clinics, regional hospital systems, to large healthcare systems.” The Report determined it was not feasible to address every cybersecurity threat across the entire U.S. healthcare industry; the report focuses on the five most prevalent threats.
This is the third of five articles that discuss the report’s findings. The first article discussed email phishing attacks. The second article discussed the threat of ransomware attacks. This third article discusses loss or theft of equipment or data.
I. What is loss or theft of equipment or data?
Every single day, mobile devices such as smartphones, tablets, laptops, and thumb drives are lost or stolen, and often find their way to a hacker’s hands. Theft of equipment and data is an ongoing threat for all organizations including healthcare providers. Through the first eight months of 2018, the Office of Civil Rights received reports of 192 theft cases affecting 2,041,668 individuals. Although the value of the device represents one loss, far greater are the consequences if a lost or stolen device contains sensitive data.
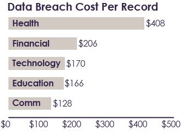
(Graph found on pg. 9 of the “Report”)
In cases where the lost device was not appropriately safeguarded or password protected, the loss may result in unauthorized or illegal access, dissemination, and use of the sensitive data. Even if the device is recovered, the data may have been erased and completely lost. Loss or malicious use of data may result in business disruption and compromised patient safety, and may require notification to patients, applicable regulatory agencies, and the media.
II. Vulnerabilities and negative impact of loss or theft of equipment or data
An organization’s vulnerabilities to loss or stolen equipment or data include (i) a lack of asset inventory and control, (ii) lack of encryption, (iii) lack of physical security practices (e.g., open offices and poor physical access management), (iv) lack of simple safeguards such as computer cable locks to secure devices within the office environment, (v) lack of awareness about the scope of the threat, (vi) lack of effective vendor security management, including controls to protect equipment or sensitive data, and (vii) lack of an “end-of-service” data destruction process to clear sensitive data before IT assets, including medical devices, are discarded or transferred. Bad actors will try to identify and then exploit these vulnerabilities if an organization does not take preventative measures to minimize or eliminate these risks.
III. Practices and tips to consider
The Report discussed several practices an organization should consider to reduce vulnerability to loss or theft of equipment or data:
- Encrypt sensitive data, especially when transmitting data to other devices or organizations;
- Implement proven and tested data backups, with proven and tested restoration of data;
- Use data loss prevention tools to detect or stop an active threat;
- Implement a mobile device policy supplemented with ongoing user awareness training on securing these devices;
- Require employees to promptly report loss/theft to designated company individuals to terminate access to the device and/or network;
- Maintain a complete, accurate, and current asset inventory of mobile phones and other mobile devices such as laptops and thump drives that contain PHI or PII;
- Encrypt data at rest on mobile devices to be inaccessible to anyone who finds the device; and
- Define a process to remove or destroy sensitive data from every device before it is retired, refurbished, or resold.
The report also discussed the following “Threat Quick Tips”:
1. If you are heading out on a business trip or personal vacation, follow the same, and possibly greater, security procedures as you do in the office. Make sure you know your organization’s policy on removing equipment from the workplace.
2. What to ask?
- Can I travel with my equipment?
- Can I take my equipment offsite to work remotely?
- Are thumb drives or other portable storage devices allowed?
- Is the information on my computer or storage device encrypted?
- Is there a secure virtual private network (VPN) that I can use, along with secure, password-protected Wi-Fi, to log into the network?
3. When to ask?
- As soon as you realize that your device or equipment has been stolen or misplaced, your supervisor and IT security professional should be notified immediately so appropriate measures can be taken to safeguard the data saved on your device or equipment.
4. Who to ask?
- Your IT security support staff or similar point of contact should be notified when a work device or equipment has been misplaced, lost, or stolen. The data saved on them is now compromised and susceptible to unauthorized access, dissemination, and use. This is a serious cyber breach and should be handled by trained IT security professionals.
The threat of loss or theft of equipment or data is one of the most dangerous, but probably easiest to prevent. With proper data encryption, strong physical security practices, simple safeguards, and awareness training, healthcare organizations can easily protect themselves from this type of attack.
More information on activities to prepare and respond to a data loss can be found in NIST Special Publication 800-184 – Guide to Cybersecurity Event Recovery.
More information on proper sanitization and destruction of data prior to disposal of devices can be found in NIST Special Publication 800-88, Revision 1, Guidelines for Media Sanitation.
Our next article will discuss another common cyberattack threatening the healthcare industry: Insiders causing accidental or intentional data loss.
Follow us on for more content updates
for more content updates